OS Probed: Red Hat EL4/EL5 - Fedora Core 5/6/7 and CentOS 4.4/5
Document version: 0.5
- Integration with: Mail Server: Postfix, Courier-IMAP, Maildrop, GNARWL, Cyrus-SASL, OpenSSL
- Redundancy: OpenLDAP Master/Slave replication
- Install methods: yum install, up2date -i
- GOsa2 release: 2.5.9-1
- Customizations: New LDAP schema that separate mail home from unix home
 Capabilities
Capabilities- Courier IMAP, the best POP3/IMAP4 Software System
- OpenSSL, for securing all connections via TLS
- Postfix, the best and flexible MTA in the world
- OpenLDAP, centralized information
- Maildrop, the best MDA that manage Quotas in LDAP
- GNARWL, the best software for vacations stored in LDAP
- Cyrus SASL, for autenticate users to use SMTP
- OpenLDAP Replication, the best way for high availability
- GOsa2, the best LDAP Administrator software
Autor
Julian Rios
jrios@sapian.org
Sapian S.A, Medellin-Colombia
INDEX
1. Processes flow
2. Installing GOsa2
3. Installing Mail Server
4. Replicating OpenLDAP
NOTES
a. In this guide "jrios.com.co" is the domain
b. mail.jrios.com.co is the MX for mail
c. The guide not have a detailed description of the steps. The "blog method" of this page is intended for resolve questios about steps. Example comment: "In part 2, step 22, how to fork_vacation.sh script works ?"
PROCESSES FLOW
1. Receiving Mail
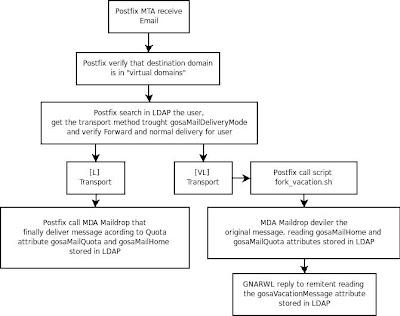
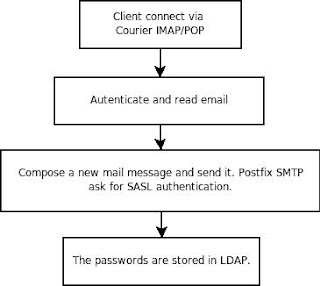
2. Reading and Sending Mail
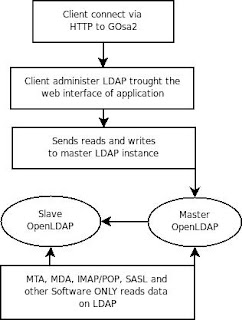
3. LDAP Administration with GOsa
STEPS FOR INSTALL GOsa2
This steps describe in form "kitchen prescription" how to install the GOsa2 package.
1. Install OpenLDAP
# yum install openldap openldap-clients openldap-servers
2. Download from GOsa2 site all the RPM Packages for Red Hat Distribution. The FTP URL is: ftp://oss.gonicus.de/pub/gosa/redhat
3. Install GOsa2 Package Prerequisites
# rpm -ivh perl-TimeDate-1.16-1.noarch.rpm
# rpm -ivh perl-MIME-Types-1.16-1.noarch.rpm
# rpm -ivh perl-MailTools-1.74-1.noarch.rpm
# rpm -ivh perl-MIME-Lite-3.01_05-1.noarch.rpm
# rpm -ivh perl-Crypt-SmbHash-0.02-1.noarch.rpm
4. Install OS Package Prerequisites
# yum install httpd
# yum install php-snmp
# yum install php-mysql
# yum install php-mbstring
# yum install php-imap
# yum install perl-ldap
5. Install GOsa2 Package
# rpm -ivh gosa-2.5.9-1.noarch.rpm
6. Install GOsa2 Schemas
# rpm -ivh gosa-schema-2.5.9-1.noarch.rpm
Download gosa_custom.schema or copy from quote:
-----
#$Id: authldap.schema,v 1.8 2005/03/20 19:10:30 mrsam Exp $
#
# OID prefix: 1.3.6.1.4.1.25981
#
# Attributes: 1.3.6.1.4.1.25981.1.1
#
# Depends on: gosa.schema and cosine.schema
attributetype ( 1.3.6.1.4.1.25981.1.1.1 NAME 'gosaMailHome'
DESC 'The absolute path to the mail message stor directory in a virtual mail setup.'
EQUALITY caseExactIA5Match
SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 SINGLE-VALUE )
#
# Objects: 1.3.6.1.4.1.25981.1.2
#
objectclass ( 1.3.6.1.4.1.25981.1.2.1 NAME 'gosaVirtualMailAccount' SUP top AUXILIARY
DESC 'Objectclass to mark Virtual MailAccounts for GOsa (v2.4)'
MAY ( gosaMailHome ) )
-----
The file gosa_custom.schema define new attribute called gosaMailHome for separate the home of Unix accounts from Mail user homes. This personalized schema must be placed in /etc/openldap/schema/gosa:
# cp gosa_custom.schema /etc/openldap/schema/gosa
7. Installing English web documentation
# rpm -ivh gosa-help-en-2.5.9-1.noarch.rpm
8. OpenLDAP /etc/openldap/slapd.conf file
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/gosa/samba3.schema
include /etc/openldap/schema/gosa/pureftpd.schema
include /etc/openldap/schema/gosa/gofon.schema
include /etc/openldap/schema/gosa/gosystem.schema
include /etc/openldap/schema/gosa/goto.schema
include /etc/openldap/schema/gosa/gosa+samba3.schema
include /etc/openldap/schema/gosa/gofax.schema
include /etc/openldap/schema/gosa/goserver.schema
include /etc/openldap/schema/gosa/goto-mime.schema
include /etc/openldap/schema/gosa/gosa_custom.schema
schemacheck on
allow bind_v2
database bdb
directory /var/lib/ldap
loglevel 256
lastmod on
suffix "dc=jrios,dc=com,dc=co"
rootdn "cn=admin,dc=jrios,dc=com,dc=co"
rootpw {MD5}RQoN6pXDXTICFTcKo+wYwQ==
index uid,mail eq
index gosaMailAlternateAddress,gosaMailForwardingAddress eq
index cn,sn,givenName,ou pres,eq,sub
index objectClass pres,eq
index uidNumber,gidNumber,memberuid eq
index gosaSubtreeACL,gosaObject,gosaUser pres,eq
index sambaSID eq
index sambaPrimaryGroupSID eq
index sambaDomainName eq
access to *
by * read
TLSCACertificateFile /etc/pki/tls/certs/ca-bundle.crt
TLSCertificateFile /etc/pki/tls/certs/slapd.pem
TLSCertificateKeyFile /etc/pki/tls/certs/slapd.pem
cachesize 100000
9. Change the rootpw password in slapd.conf file
# slappasswd -h {MD5}
Put the result string in file
10. TLS Certificate for OpenLDAP
Depending of the distribution, the .pem and .crt files are in other path. Search them with:
# find / -name 'slapd.pem'
# find / -name 'ca-bundle.crt'
And change the path in slapd.conf file
11. Enable OpenLDAP logs from /etc/syslog.conf
local4.* /var/log/ldap
12. Restart syslog service
# service syslog restart
13. Start OpenLDAP now
# service ldap start
14. Create initial.ldif file for insert base information to OpenLDAP
dn: dc=jrios,dc=com,dc=co
dc: jrios
objectClass: top
objectClass: domain
dn: ou=groups,dc=jrios,dc=com,dc=co
objectClass: organizationalUnit
ou: groups
dn: ou=people,dc=jrios,dc=com,dc=co
objectClass: organizationalUnit
ou: people
dn: cn=admin,ou=people,dc=jrios,dc=com,dc=co
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: gosaAccount
uid: admin
cn: admin
givenName: admin
sn: GOsa Main Administrator
sambaLMPassword: 10974C6EFC0AEE1917306D272A9441BB
sambaNTPassword: 38F3951141D0F71A039CFA9D1EC06378
userPassword:: dGVzdGVy
dn: cn=administrators,ou=groups,dc=jrios,dc=com,dc=co
objectClass: gosaObject
objectClass: posixGroup
gosaSubtreeACL: :all
cn: administrators
gidNumber: 999
memberUid: admin
15. Add initial.ldif information to OpenLDAP
# ldapadd -x -D "cn=admin,dc=jrios,dc=com,dc=co" -h localhost -W -f initial.ldif -v
16. Edit /etc/php.ini file and modify values for
session.gc_maxlifetime = 100000
memory_limit = 100M
17. Start web server
# service httpd start
18. Setup GOsa2 from web interface
a. Point your browser to http://localhost/gosa. Click Continue button, ignoring this:
checking for mhash module
checking for cups module
checking for kadm5 module
b. Click Continue button, ignoring this:
Checking for fping utility
php.ini check -> magic_quotes_gpc
c. Set URI, and click Continue button:
ldap://localhost:389
d. Complete the form and click Continue Button:
Location Name: Corporation
Admin DN: cn=admin,dc=jrios,dc=com,dc=co
Admin password: *****
Base: dc=jrios,dc=com,dc=co
People storage ou: ou=people
People dn attribute: uid
Group storage ou: ou=groups
ID base for users/groups: 1000
Encryption algorithm: md5
Mail method: disable
Display PHP errors: true
e. Click Download configuration Button and save gosa.conf in a local folder
19. Copy file gosa.conf to /etc/gosa directory and apply permissions
# chown root.apache /etc/gosa/gosa.conf
# chmod 640 /etc/gosa/gosa.conf
20. Click Retry Button
21. Login to web interface of Gosa with admin account:
Login: admin
Password: tester
NOTE: The user admin for gosa is diferent from admin for LDAP !, In this case, the password for admin is "tester". This user admin have a following dn:
cn=admin,ou=people,dc=jrios,dc=com,dc=co
This password "tester" come from initial.ldif file.
22. Configuring GOsa. File /etc/gosa/gosa.conf
In this case, we are using GOsa only for this proposal:
a. Manage Mail and user Accounts
In this file, we need deactivate all other options, plugins, etc. Section need look like this:
section name="My account"
plugin acl="default" class="user" icon="personal.png"
path="plugins/personal/generic"
plugin acl="default" class="mailAccount" icon="email.png"
Path="plugins/personal/mail"
plugin acl="default" class="password" icon="password.png"
path="plugins/personal/password"
section
In the section Administration, we need delete plugins: oGroupManagement, applicationManagement, FAIclass, blocklists, goFonMacro and conference. Finally, need look like this:
section name="Administration"
plugin acl="user" class="userManagement" icon="user.png"
path="plugins/admin/users"
plugin acl="group" class="groupManagement" icon="group.png"
path="plugins/admin/groups"
plugin acl="department" class="departmentManagement" icon="department.png"
path="plugins/admin/departments"
plugin acl="application" class="applicationManagement"
icon="application.png" path="plugins/admin/applications"
plugin acl="systems" class="systems" icon="system.png"
path="plugins/admin/systems"
section
In the Addons section, we only need addressbook and ldapmanager. This are good utilities:
section name="Addons"
plugin acl="addressbook" class="addressbook" icon="addressbook.png"
path="plugins/addons/addressbook"
plugin acl="ldapmanager" class="ldif" icon="ldif.png"
path="plugins/addons/ldapmanager"
section
tab class="user" name="Generic"
tab class="mailAccount" name="Mail"
postcreate="/usr/bin/sudo /etc/gosa/createmail.sh %uid ;
/usr/bin/sudo /etc/gosa/createhome.sh %uid"
usertabs
Note that "postcreate" call two scripts, one for create mail home directory and one for insert the necesary attributes in LDAP for manage this homes directories.
In grouptabs section we only need:
tab class="group" name="Generic"
tab class="acl" name="ACL"
grouptabs
23. Restart services and configure the automatic start
# service httpd restart
# service ldap restart
# chkconfig --level 345 httpd on
# chkconfig --level 345 ldap on
24. Create postscript file /etc/gosa/createmail.sh. This script create the homes for the mail users.
#!/bin/bash
/usr/bin/sudo mkdir /var/vmail/$1
/usr/bin/sudo /usr/lib/courier-imap/bin/maildirmake /var/vmail/$1/Maildir
/usr/bin/sudo /bin/chown -R vmail.vmail /var/vmail/$1
/usr/bin/sudo /bin/chmod -R 2770 /var/vmail/$1
25. Create postscript file /etc/gosa/createhome.sh. This script create the mail home attribute for the mail users.
Attention to password !
#!/bin/bash
LDAPDN=`ldapsearch -h localhost -x -b "dc=jrios,dc=com,dc=co"\
-D "cn=admin,dc=jrios,dc=com,dc=co" -w jrios "(uid=$1)" | grep dn`
(
echo ""
echo "$LDAPDN"
echo "changetype: modify"
echo "add: objectClass"
echo "objectClass: gosaVirtualMailAccount"
echo ""
echo "$LDAPDN"
echo "changetype: modify"
echo "add: gosaMailHome"
echo "gosaMailHome: /var/vmail/$1"
) | ldapmodify -a -x -D "cn=admin,dc=jrios,dc=com,dc=co" -w jrios -h localhost -v
26. Adjust permissions to postcreate scripts
# chmod a+x /etc/gosa/createhome.sh
# chmod a+x /etc/gosa/createmail.sh
27. Enable apache sudoer for execute this scripts. In file /etc/sudoers:
apache ALL=(ALL) NOPASSWD: /etc/gosa/createhome.sh, /etc/gosa/createmail.sh
Also, if the line "Defaults requiretty" is set, we need comment them !
STEPS FOR INSTALL MAIL SERVER
This steps describe in form "kitchen prescription" how to install a powerful email system.
1. Create user vmail
# groupadd -g 5000 vmail
# useradd -m -d /var/vmail -g 5000 -u 5000 vmail
# chmod 2775 /var/vmail
2. Installing Postfix MTA, and disabling sendmail
# service sendmail stop
# rpm -e sendmail-cf
# rpm -e sendmail
# chkconfig --level 345 sendmail off
# yum install postfix*
3. Installing OS prerequisites for compiling Courier Packages
# yum install mysql-devel
# yum install openldap-devel
# yum install postgresql-devel
# yum install gcc-c++
# yum install gdbm-devel
# yum install pam-devel
# yum install expect
# yum install libtool-ltdl*
# yum install pcre*
4. Download Courier Packages (IMAP, Authlib and Maildrop)
Point your browser to www.courier-mta.org and download files named:
a. courier-authlib-0.59.1.tar.bz2
b. courier-imap-4.1.2.tar.bz2
c. maildrop-2.0.3.tar.bz2
5. With an unprivileged user do:
$ cd
$ mkdir -m 755 rpm
$ mkdir -m 755 rpm/BUILD
$ mkdir -m 755 rpm/RPMS
$ mkdir -m 755 rpm/SOURCES
$ mkdir -m 755 rpm/SPECS
$ mkdir -m 755 rpm/SRPMS
6. Create .rpmmacros file:
$ vi .rpmmacros
%_topdir /home/jrios/rpm
%packager Sapian
7. Build Courier Authlib package
$ rpmbuild -ta courier-authlib-0.59.1.tar.bz2
8. Install Courier Authlib now
$ cd ~/rpm/RPMS/i386
$ su root
# rpm -ivh courier-authlib-0.59.1-1.fc6.i386.rpm
# rpm -ivh courier-authlib-devel-0.59.1-1.fc6.i386.rpm
9. Preparing compilation of Courier IMAP
$ cd
$ tar tvjf courier-imap-4.1.2.tar.bz2 | grep spec
$ tar xvjf courier-imap-4.1.2.tar.bz2 courier-imap-4.1.2/courier-imap.spec
$ mv courier-imap-4.1.2/courier-imap.spec rpm/SPECS/
$ rmdir courier-imap-4.1.2
$ mv courier-imap-4.1.2.tar.bz2 rpm/SOURCES/
10. Modifying /home/jrios/rpm/SPECS/courier-imap.spec file
Replace this:
%if %suse_version
BuildPreReq: rpm >= 3.0.5 /usr/bin/sed openldap2 openldap2-devel %([ %
{suse_version} -gt 819 ] && echo fam-devel)
%else
BuildPreReq: rpm >= 4.0.2 sed fam-devel openldap-devel openldap-servers
%endif
For this:
%if %suse_version
BuildPreReq: rpm >= 3.0.5 /usr/bin/sed openldap2 openldap2-devel
%else
BuildPreReq: rpm >= 4.0.2 sed openldap-devel openldap-servers
%endif
11. Build Courier IMAP
$ rpmbuild -ba ~/rpm/SPECS/courier-imap.spec
12. Install complete Courier IMAP now
# rpm -ivh rpm/RPMS/i386/courier-authlib-ldap-0.59.1-1.fc6.i386.rpm
# rpm -ivh rpm/RPMS/i386/courier-imap-4.1.2-1.6.i386.rpm
13. Compile Maildrop MDA
# tar xjvf maildrop-2.0.3.tar.bz2
# cd maildrop-2.0.3
# ./configure --enable-maildirquota --enable-maildrop-uid=5000 --enable-maildrop-gid=5000 -enable-authlib
# make
# make install
# chown root /usr/local/bin/maildrop
# chmod u+s /usr/local/bin/maildrop
# chmod a+rx /var/spool/authdaemon/
14. Download GNARWL software
Point your web browser at http://www.home.unix-ag.org/patrick/index.php?gnarwl and download package named gnarwl-3.3.tgz
15. Compile GNARWL for LDAP vacations
# tar xzvf gnarwl-3.3.tgz
# cd gnarwl-3.3
# ./configure
# make
# make install
# make perm
16. Install Cyrus-SASL
# yum install cyrus-sasl*
17. Adjust File /usr/local/etc/gnarwl.conf
map_sender $sender
map_receiver $recepient
map_subject $subject
map_field $fullname cn
map_field $deputy mail
server localhost
port 389
scope sub
login cn=admin,dc=jrios,dc=com,dc=co
password jrios
protocol 3
base dc=jrios,dc=com,dc=co
queryfilter (|(mail=$recepient)(gosaMailAlternateAddress=$recepient))
result gosaVacationMessage
blockfiles /usr/local/var/lib/gnarwl/block/
umask 0644
blockexpire 0
mta /usr/sbin/sendmail -F $recepient -t $sender
maxreceivers 64
maxheader 512
charset ISO8859-1
badheaders /usr/local/var/lib/gnarwl/badheaders.db
blacklist /usr/local/var/lib/gnarwl/blacklist.db
forceheader /usr/local/var/lib/gnarwl/header.txt
forcefooter /usr/local/var/lib/gnarwl/footer.txt
recvheader To Cc
loglevel 3
18. Configuring Postfix in /etc/postfix/main.cf file
queue_directory = /var/spool/postfix
command_directory = /usr/sbin
daemon_directory = /usr/libexec/postfix
mail_owner = postfix
smtpd_banner = mail.jrios.com.co
myhostname = mail.jrios.com.co
myorigin = jrios.com.co
mydestination = mail.jrios.com.co
mynetworks = 127.0.0.0/8, 10.0.0.0/8
alias_maps = hash:/etc/aliases, ldap:virtualaliases
alias_database = hash:/etc/aliases
virtual_mailbox_limit = 50000000000
message_size_limit = 25728640
virtual_mailbox_domains = jrios.com.co, gosa.jrios.com.co
virtual_mailbox_base = /var/vmail
virtual_uid_maps = static:800
virtual_gid_maps = static:800
mailbox_size_limit = 50000000000
recipient_delimiter =
inet_interfaces = all
home_mailbox = Maildir/
smtpd_recipient_restrictions = permit_mynetworks,
permit_sasl_authenticated,
check_recipient_access ldap:chkuser,
reject_unauth_destination,
reject_non_fqdn_hostname,
reject_non_fqdn_sender,
reject_non_fqdn_recipient,
reject_unknown_sender_domain,
reject_unknown_recipient_domain,
reject_unauth_pipelining,
reject_unauth_destination,
permit
# RFC standars
smtpd_helo_required = yes
strict_rfc821_envelopes = yes
disable_vrfy_command = yes
# RBL checks and restrictions
smtpd_client_restrictions = permit_mynetworks,
permit_sasl_authenticated,
reject_rbl_client combined.njabl.org,
reject_rbl_client dul.dnsbl.sorbs.net,
reject_rbl_client zen.spamhaus.org,
reject_rbl_client opm.blitzed.org,
reject_rbl_client dialups.mail-abuse.org,
reject_rbl_client cbl.abuseat.org,
reject_rbl_client bl.spamcop.net,
reject_unauth_pipelining
# Transport config
[L]_destination_concurrency_limit = 1
[L]_destination_recipient_limit = 1
[VL]_destination_concurrency_limit = 1
[VL]_destination_recipient_limit = 1
virtual_transport = [L]
local_transport = [L]
virtual_maps = hash:/etc/postfix/virtual, ldap:virtualaliases
transport_maps = hash:/etc/postfix/transport, ldap:tmap
# LDAP transport source
tmap_server_host = 127.0.0.1
tmap_search_base = dc=jrios,dc=com,dc=co
tmap_query_filter = (|(mail=%s)(gosaMailAlternateAddress=%s))
tmap_result_attribute = gosaMailDeliveryMode
tmap_cache = no
tmap_bind = yes
tmap_bind_dn = cn=admin,dc=jrios,dc=com,dc=co
tmap_bind_pw = jrios
# GoSA main LDAP source
virtualaliases_server_host = 127.0.0.1
virtualaliases_server_port = 389
virtualaliases_bind = no
virtualaliases_timeout = 5
virtualaliases_search_base = dc=jrios,dc=com,dc=co
virtualaliases_query_filter = (|(mail=%s)(gosaMailAlternateAddress=%s))
virtualaliases_result_attribute = gosaMailForwardingAddress,mail
# Recipient Validation
chkuser_server_port = 389
chkuser_bind = yes
chkuser_bind_dn = cn=admin,dc=jrios,dc=com,dc=co
chkuser_bind_pw = jrios
chkuser_timeout = 5
chkuser_search_base = dc=jrios,dc=com,dc=co
chkuser_query_filter = (|(mail=%s)(gosaMailAlternateA
chkuser_result_attribute = gosaMailForwardingAddress,mail
chkuser_result_format = OK
# SSL/TLS config
smtp_use_tls = yes
smtpd_use_tls = yes
smtp_tls_note_starttls = yes
smtpd_tls_key_file = /etc/postfix/ssl/smtpdkey.pem
smtpd_tls_cert_file = /etc/postfix/ssl/smtpd.pem
smtpd_tls_loglevel = 1
# SASL config
smtpd_sasl_auth_enable = yes
smtpd_sasl_application_name = smtpd
smtpd_sasl_security_options = noanonymous
smtpd_sasl_local_domain =
broken_sasl_auth_clients = yes
19. Set hostname in /etc/hosts file
Acording to your server private IP address:
192.168.1.1 mail.jrios.com.co jrios.com.co
20. Create SSL certificates for Postfix
First, make sure that file openssl.cnf is in the specified path, otherwise find it
# mkdir /etc/postfix/ssl
# /usr/bin/openssl req -config /etc/pki/tls/openssl.cnf -new -x509 -nodes -out /etc/postfix/ssl/smtpd.pem -keyout /etc/postfix/ssl/smtpdkey.pem -pem -days 999999
21. Configuring Postfix in /etc/postfix/master.cf file
Make sure that you have the following lines:
smtps inet n - n - - smtpd
-o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes
submission inet n - n - - smtpd
-o smtpd_enforce_tls=yes -o smtpd_sasl_auth_enable=yes -o smtpd_etrn_restrictions=reject
[L] unix - n n - - pipe
flags=DRhu user=vmail argv=/usr/local/bin/maildrop -w 80 -d ${recipient}
[VL] unix - n n - - pipe
flags=F user=adminvac argv=/usr/local/bin/fork_vacation.sh $sender $recipient
22. Creating file /usr/local/bin/fork_vacation.sh for manage vacations
#!/bin/bash
ORIGIN="$1"
DESTINY="$2"
/usr/bin/sudo -u vmail /usr/local/bin/maildrop -w 90 -d $DESTINY
/usr/bin/sudo -u gnarwl /usr/local/bin/gnarwl -s $ORIGIN -a $DESTINY
23. Set permissions to file /usr/local/bin/fork_vacation.sh
# chmod 755 /usr/local/bin/fork_vacation.sh
24. Create user adminvac with sudo for execute the vacation binary
# adduser adminvac
# vi /etc/sudoers
adminvac ALL=(ALL) NOPASSWD: ALL
25. Starting Postfix
# postmap /etc/postfix/transport
# postmap /etc/postfix/virtual
# newaliases
# service postfix start
26. Automatic start for Postfix
# chkconfig --level 345 postfix on
27. Configuring Courier Authlib /etc/authlib/authdaemonrc file
authmodulelist="authldap"
28. Configuring Courier Authlib /etc/authlib/authldaprc file
LDAP_SERVER localhost
LDAP_URI ldap://localhost
LDAP_PORT 389
LDAP_PROTOCOL_VERSION 3
LDAP_BASEDN dc=jrios,dc=com,dc=co
LDAP_BINDDN cn=admin,dc=jrios,dc=com,dc=co
LDAP_BINDPW jrios
LDAP_TIMEOUT 120
LDAP_AUTHBIND 1
LDAP_MAIL mail
LDAP_FILTER (objectClass=gosaMailAccount)
LDAP_GLOB_UID vmail
LDAP_GLOB_GID vmail
LDAP_HOMEDIR gosaMailHome
LDAP_MAILDIR gosaMailHome/Maildir
LDAP_MAILDIRQUOTA gosaMailQuota
LDAP_FULLNAME cn
LDAP_CRYPTPW userPassword
LDAP_DEREF never
LDAP_TLS 0
29. Configuring Cyrus SASL /etc/saslauthd.conf (create file)
ldap-servers: ldap://localhost/
ldap_auth_method: bind
ldap_bind_dn: cn=admin,dc=jrios,dc=com,dc=co
ldap_bind_pw: jrios
ldap_filter: (uid=%U)
ldap_search_base: dc=jrios,dc=com,dc=co
30. File /etc/sysconfig/saslauthd
START=yes
MECH="ldap"
PWDIR="/var/run/saslauthd"
PARAMS="-O /etc/saslauthd.conf -m ${PWDIR}"
31. File /usr/lib/sasl2/smtpd.conf
pwcheck_method: saslauthd
mech_list: plain login
32. Configuring and tunning Maildrop /etc/maildroprc (create file)
SHELL="/bin/bash"
DEFAULT = "Maildir/"
MAILDIR = "Maildir/"
`reformail -D 8000 duplicate.cache`
if ( $RETURNCODE == 0 )
exit
33. Start and Automatic start Courier/Cyrus Applications
# service courier-authlib start
# service courier-imap start
# service saslauthd start
# chkconfig --level 345 courier-authlib on
# chkconfig --level 345 courier-imap on
# chkconfig --level 345 saslauthd on
34. Creating Mail Server in GOsa2 web interface
a. Login to web interface
b. Click on Systems link
c. Click on New Server button
d. Complete the Generic Tab
Server name: Mail
Description: Mail server
IP-address: 127.0.0.1
MAC-address: 00:18:FE:77:41:C2
Mode: Activated
e. Complete the Databases Tab
Click IMAP Admin access
Server Identifier: localhost
Connect URL: {localhost:143}
Admin user: noadmin
Password: none
Sieve Port: 2000
f. Complete Services Tab
Click Mail Server
g. Click on Save Button
35. Create one user for Mail
a. Login to web interface
b. Click on Users link
c. Click on Create new user button
Last name: Rios
First name: Julian
Login: julian
d. Click on Mail Tab
Click on Crate Mail Account button
Primary address: julian@jrios.com.co
Server: localhost
Click on Save button
Choose a password for User
Create account gnarwl@jrios.com.co, flollowing the same past steps.
Maildrop use Quotas in following format: 5000000S indicates aprox 5 MB of quota (5000000 bytes). The quota text box in the Mail Tab of GOsa not accept this value (the character S is not valid number). GOsa show this error when the administrator set this 5 MB (5000000S) quota value:
An error ocurred while processing your request: Value in 'Quota Size' is not valid
The solution is modify the code of GOsa ! Is simply:
a. In file /usr/share/gosa/plugins/personal/mail/class_mailAccount.inc change these lines:
/* Check quota */
if ($this->gosaMailQuota != '' && chkacl ($this->acl, "gosaMailQuota") == ""){
if (!is_numeric($this->gosaMailQuota)) {
$message[]= _("Value in 'Quota size' is not valid.");
} else {
$this->gosaMailQuota= (int) $this->gosaMailQuota;
}
}
For these lines:
/* Check quota */
//if ($this->gosaMailQuota != '' && chkacl ($this->acl, "gosaMailQuota") == ""){
//if (!is_numeric($this->gosaMailQuota)) {
//$message[]= _("Value in 'Quota size' is not valid.");
//} else {
//$this->gosaMailQuota= (int) $this->gosaMailQuota;
$this->gosaMailQuota= $this->gosaMailQuota;
//}
//}
Note the comment lines. Also, supress (int) in the line that insert the quota value. Now, we can insert correctly the 5000000S value, and Maildrop run perfectly with this.
b. In file /usr/share/gosa/include/class_mail-methods.inc the function connect need look like this:
function connect($gosaMailServer)
{
return (FALSE);
}
c. In file /usr/share/gosa/include/class_mail-methods.inc the function getQuota need look like this:
function getQuota($folder)
{
$result= array('quotaUsage' => '0', 'gosaMailQuota' => '');
$quota_value = @imap_get_quota($this->mbox, $folder);
return ($result);
}
STEPS FOR INSTALL OPENLDAP REPLICATION
This steps describe in form "kitchen prescription" how to install in diferent servers 2 instances of ldap to gain high availability for the enterprise solution.
1. Configure Openldap master server for replication in /etc/openldap/slapd.conf file
After the indexing options put:
replogfile /var/lib/ldap/replog
replica host=slaveldap:389
binddn="cn=admin,dc=jrios,dc=com,dc=co"
bindmethod=simple credentials="jrios"
2. Make a "dump" of ldap database to dump.ldif file
# slapcat > /tmp/dump.ldif
3. Stop the master and slave ldap server
# service ldap stop
4. In the slave server, restore the master ldap dump
# slapadd -b "dc=jrios,dc=com,dc=co" -l dump.ldif -f /etc/openldap/slapd.conf
5. Adjust permissions to database in slave server
# chown ldap:ldap /var/lib/ldap/*
6. In the slave server, put these lines in /etc/openldap/slapd.conf
After the indexing options,
updatedn "cn=admin,dc=jrios,dc=com,co"
updateref ldap://masterldap
7. Start ldap servers, first slave and then master
# service ldap start
Free Counter